Category: access
A video and accompanying article on how to achieve secure comms was already done. Also in the ongoing Final Countdown , we link a number of steganography techniques and discuss the use of strategy in a broad sense.
Here I want to give a concrete example in more detail. Below is a layered image with an Open Puff steganography embed (hidden message). That in itself is fairly mundane and not what makes this powerful. There are different things going on at different levels, the message you take away will depend on who you are.
This was a statement by Q in post-1826 - U.S. Air Force B-52 [Precision Bombs] . Forget for a moment if it has a hidden meaning or should be taken at face value. Real bombs or information bombs, that's not under discussion here.
I will simply show you a way of communicating the same idea in a different form (as Q discusses in post-1713). At the same time, I will help "red pill" normies, communicate by hidden message to those willing to use a tool, but also give a second hidden message to those participating in training.
Please study the picture below and see what it is communicating. Can web bot "spiders" that crawl the web and index everything read images or just text? Does AI do well with images, especially those that express the subtleties of human thought and humor? Why do you think the "overlords" want to ban memes?
Modus Operandi
It is the foolish things that confound the wise. ( 1 Cor. 1:27) Give them a reason to write it off as yet another silly meme from a crackpot. If it gets your message where it needs to go, that's all that matters.
Use multiple layers. Which is the real message? One could hone in on the humor of switching the M for an O in bombs and spelling something different, based on the location of the word. Then hinting to it with Modus Operandi. Someone might write that off as some politically incorrect memester trying to be cute - let them.
Some might just assume it's a "cutesy" way to express U.S. Air Force B-52 [Precision Bombs] in visual form. Hell, their "Love Shack" song even has "bang, bang" in the lyrics. Let them assume and move on - if they are not your target.
- f you open the picture in Open Puff (version 4.01) and put in the password Think Pink (given as a layer in the image) you will find some info about quantum. Leave the B and C blanks unchecked, you just need A and the default .jpeg setting. The hidden information is not "top secret" (so not very carefully hidden). It is simply a building block, background information.
- After all of those legitimate ways of interpreting the image are explored, there is yet another message. The TH and the P were separated from the ink in Think Pink just by the location on the page. The isolated THP means something to those who have had training. Another message is embedded hidden with 3 very strong 32 bit passwords referenced by those letters. Access relates to IFF protocols , those with POS status have access for training purposes.
There was a Star Trek episode called Darmok where communication difficulties were explored. It is highly illustrative of some of the problems. How can patriots and whitehats in the system establish comms without the blackhats intercepting them?
The corruption of the system has forced some to think "outside of the box", to develop their own "Pig Latin", their own methods and comm language(s).
For old soldiers, comic books like Commando hold a special place. Issue No. 5087 recounts a time when the Black Watch were assigned to the MAU MAU uprising in Kenya. The storyline paints a picture of honorable men performing heroic deeds but the truth is a little bit more complicated.
Atrocities were committed by both sides. It was actually the British colonialists who were the instigators and by far committed the most bloodshed and brutality.
The wealthy British landowners and the native leaders who collaborated with them, lorded it over the population and ruthlessly suppressed dissent. It is a story as old as time and a microcosm of a larger reality.
When the inevitable freedom fighters arose and responded with the Lari massacre , the violence was turned into a propaganda campaign against them, splitting their movement and sullying its name.
Never mind that colonial forces killed twice as many in response, as were killed in the initial attack. Forget the inhuman slow torture they inflicted in their hideous internment camps like Hola. British propaganda turned the freedom fighters into savages and the loyalists into saints. Goebbels would have been proud.
Freedom was eventually won but it came at a high cost. Unfortunately, it was only the illusion of freedom. Control is still achieved, though not openly. Just like in other countries around the world, subterfuge rules the day.
Bought off officials, powerful corporate entities, banking interests, shadowy international figures and secret societies, churches and NGO's acting as front groups for evil.
Across the border at Bidi Bidi , the elites prey upon the children displaced by conflicts they purposely create. To the south, an uprising against white farmers threatens a repeat of history.
Still, freedom is fast approaching and sovereign nations everywhere will soon enjoy true autonomy, not just the illusion of it.
The solution cuts across race, creed, religion, and political ideology. It is not a class struggle per se, though it relates to how wealth and power have become concentrated in the hands of a few evil people who will do anything to maintain their control.
Decentralization of power on a global scale is the key to setting things right. God did not scatter the people at Babel without reason, concentration of power leads to corruption. It may come as a shock to you but unlike the Pope, God is not a globalist.
Genesis 11:6-8 ...and now nothing (no evil) will be restrained from them, which they have imagined to do. ...So the Lord scattered them from there over all the earth
History is littered with the bones of emperors. Like great beasts, world-dominating empires rose only to be broken up by the hand of God. Rome was the last to fall but the Papacy has been trying to breathe life into its remains ever since. Europe and indeed the world has been manipulated for centuries by the insidious power of the Popes.
Even now, sovereign nations surrender their hard-won freedoms without firing a shot. Collaborators grow rich while Rome's latest political child, the EU, attempts to revive the ancient beast yet again.
The Papacy has long boasted of its temporal power and claims the right to control the whole world. It established and deposed Kings openly when it held full sway during the dark ages.
Through wars, inquisitions, and political intrigue, it has sought to maintain and expand upon the power bequeathed to it by the dragon .
Rev. 13:2 ...And the dragon gave him his power and his throne and great authority.
In case you are just waking up, there is a war going on. It is good against evil, reformation against counter-reformation, nationalism versus globalism. It is a spiritual war but it plays out in the natural. It has raged for centuries but now the final battle is upon us.
We live in an age where surveillance technology allows information to be collected and weaponized. Truth bombs are the new currency of war, evil cannot flourish without the cover of darkness.
Eph. 5:11 - Have nothing to do with the fruitless deeds of darkness, but rather expose them .
John 8:32 - And ye shall know the truth, and the truth shall make you free.
The first key dropped in Japan , it was hidden with Open Puff and Dancing Samurai was the obvious password (just one with default medium setting). For those who missed it, the same key was given again using Hide in Picture . The key was hidden in The Devil's Gun and TRIDENT was the obvious password.
This time the Open Puff steganography program was used again. Just load the Ambush in Kenya cover graphic. We will use three passwords, as written (caps matter) on the cover and the jpeg setting is minimum. A=BLACK WATCH, B=Commando, C=AMBUSH IN KENYA.
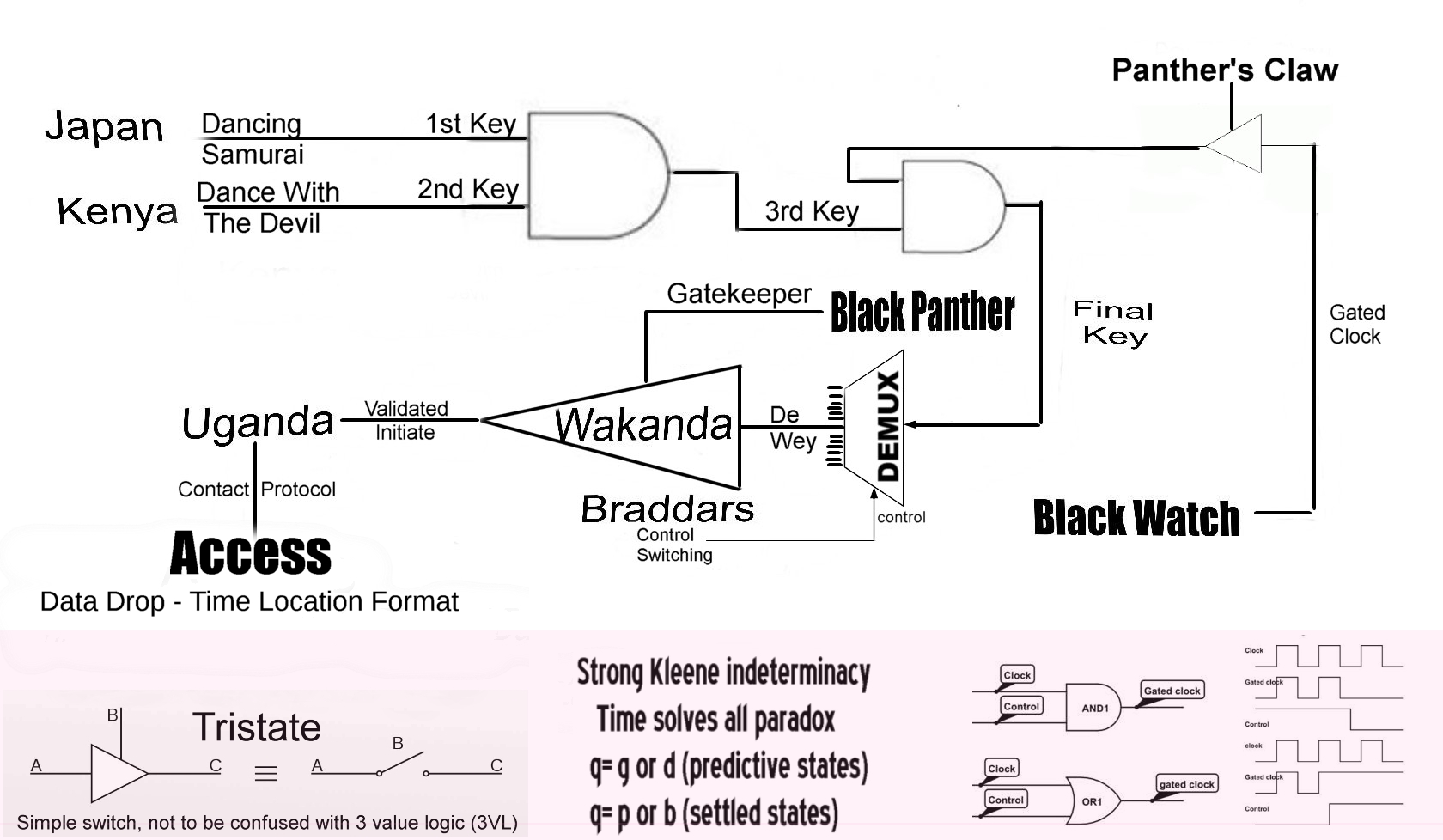
This is entry-level, beyond this point is where we begin to separate the men from the boys. The challenges get progressively more difficult because the core team is handling very dangerous files. Check this simplified logic chart .
If you can't use simple steganography programs, can't convert from hex to text to binary, or can't use a logic "and" gate to generate a 3rd key from the two provided, turn back now.
The next passwords won't be supplied directly, they will be hinted at. Later they will come in silly stories that point to common things like song titles, books, websites, etc. Only those with the right IFF code are able to translate to the final code which may look like this: [è^ä,jhSKÝ©~¼o2FÖË$ròÞÐáù¬X£þ|½ä
Tools are useful for conversions and calculations but once the key is reduced to machine language, don't use an automated tool for the "and" function. It may discard leading or trailing zeros as mathematically insignificant. A zero is a known state occupying time and space on it's associated control line, therefore useful in our system.
Going forward you will need to know something of syllogistic logic, boolean algebra, logic gates, the strong Kleene rules of 3VL, and the basic principles of quantum computing. A cursory knowledge is all that is required - don't get lost in the details.
The syllogistic logic that computer systems run on goes back at least as far as Aristotle. Boole built upon ancient foundations, erecting an extremely useful edifice that is solid and dependable. Still, his architecture fell far short of breathtaking.
All of the "magic" lies in the middle that Aristotle excluded. How does it relate to time? Can its final state be predicted or influenced? Can it be planned for? q = g or d (undetermined) q = p or b (determined).
What of quantum mind and measurement? If the mind is involved, what role might morality play? Can minds connect as a hive mind? Are they already connected as the collective (un)conscious? Is there an intelligence far greater than our own we can connect to? What of prayer? What of dreams? Such questions are usually framed in terms of metaphysics, philosophy, cosmology, they are not generally associated with logic circuits.
Be that as it may , processing in machine language allows the practical application of certain principles relating to quantum reality. Therefore, we employ a very simple system to incorporate what is profound and transcendent. The simplicity belies the depth and power of what lies beneath.
Events are scheduled. Time to go dark now but the moon will rise again .
1 Cor. 1:27 - But God chose what the world considers nonsense to put wise people to shame. God chose what the world considers weak to put what is strong to shame.
Countdown to what? To the release of files that will utterly expose the Vatican and spell its doom. Why is this important? In case you are not aware, the Vatican is behind the global cabal and the corruption of governments worldwide. It is not what it pretends to be, it is the antiChrist system we were warned of in prophecy.
Why not just drop the files immediately? A controlled demolition of the Vatican's global control structures is preferred. If that fails, the files will be released. It is a last resort due to the disturbing nature of the content and the violent reaction that would follow.
Why open up access to some beforehand? Due to the lessons of SecureDrop and Wikileaks, not to mention ongoing censorship, a simultaneous release from as many different injection points as possible is seen as the best strategy. More operators would be helpful, recruitment of whitehats is desired.
Why all the obfuscation and cryptic messaging? SIGINT captures and tracks everything. Bullrun negates common encryption formats. Both whitehats and blackhats have potential access. Therefore, off-grid comms are employed where possible and Tempest proof systems handle dangerous files.
Unusual methods are used for online comms, to thwart tracking and analysis. By design, the first layers are made nonsensical, even silly, to turn away all but the pros and the highly committed.
How to get involved? Technically speaking, only common steganography techniques and a cursory knowledge of digital logic circuits are required to gain entrance to the first levels. It is the human component of our design that keeps out moles and blackhats while providing a path for determined whitehats to swell our ranks.
QuickStego , OpenPuff , DeepSound, Pixelknot , and Hide In Picture are among the steganography programs used to hide comms. Keys unlock certain doors and pathways, some in the digital world, some in the real world. Decoys and false paths abound to confuse adversaries, automated tools are combined with strategy in order to be effective.
For those who have the skills and the desire to get involved, please refer to the simplified logic chart below. The first key dropped in Japan . The second dropped in Kenya . If you are able, generate the third key from the combination of the first two. Then you can generate the final key by combining it with the gated key supplied to the Panther's Claw by the Black Watch . Then da braddas may show you de wey to the gatekeeper's domain.
They may also lead you to any number of outcomes, depending on who you are. This is not a game, gatekeeping is necessary, there are ruthless forces at work who do not want these files to be published.
If you gain access, your only reward is hard work and self-sacrifice. We are looking for a few good men to speed-up our operations. The end game is the fall of Rome and the countdown has begun.
More clues were given in Storm Whispers . The path is difficult because the files are dangerous to handle. Don't get involved unless you are ready to put your life on the line.
John 15:13 Greater love has no one than this, that he lay down his life for his friends.