The Final Countdown

Countdown to what? To the release of files that will utterly expose the Vatican and spell its doom. Why is this important? In case you are not aware, the Vatican is behind the global cabal and the corruption of governments worldwide. It is not what it pretends to be, it is the antiChrist system we were warned of in prophecy.
Why not just drop the files immediately? A controlled demolition of the Vatican's global control structures is preferred. If that fails, the files will be released. It is a last resort due to the disturbing nature of the content and the violent reaction that would follow.
Why open up access to some beforehand? Due to the lessons of SecureDrop and Wikileaks, not to mention ongoing censorship, a simultaneous release from as many different injection points as possible is seen as the best strategy. More operators would be helpful, recruitment of whitehats is desired.
Why all the obfuscation and cryptic messaging? SIGINT captures and tracks everything. Bullrun negates common encryption formats. Both whitehats and blackhats have potential access. Therefore, off-grid comms are employed where possible and Tempest proof systems handle dangerous files.
Unusual methods are used for online comms, to thwart tracking and analysis. By design, the first layers are made nonsensical, even silly, to turn away all but the pros and the highly committed.
How to get involved? Technically speaking, only common steganography techniques and a cursory knowledge of digital logic circuits are required to gain entrance to the first levels. It is the human component of our design that keeps out moles and blackhats while providing a path for determined whitehats to swell our ranks.
QuickStego , OpenPuff , DeepSound, Pixelknot , and Hide In Picture are among the steganography programs used to hide comms. Keys unlock certain doors and pathways, some in the digital world, some in the real world. Decoys and false paths abound to confuse adversaries, automated tools are combined with strategy in order to be effective.
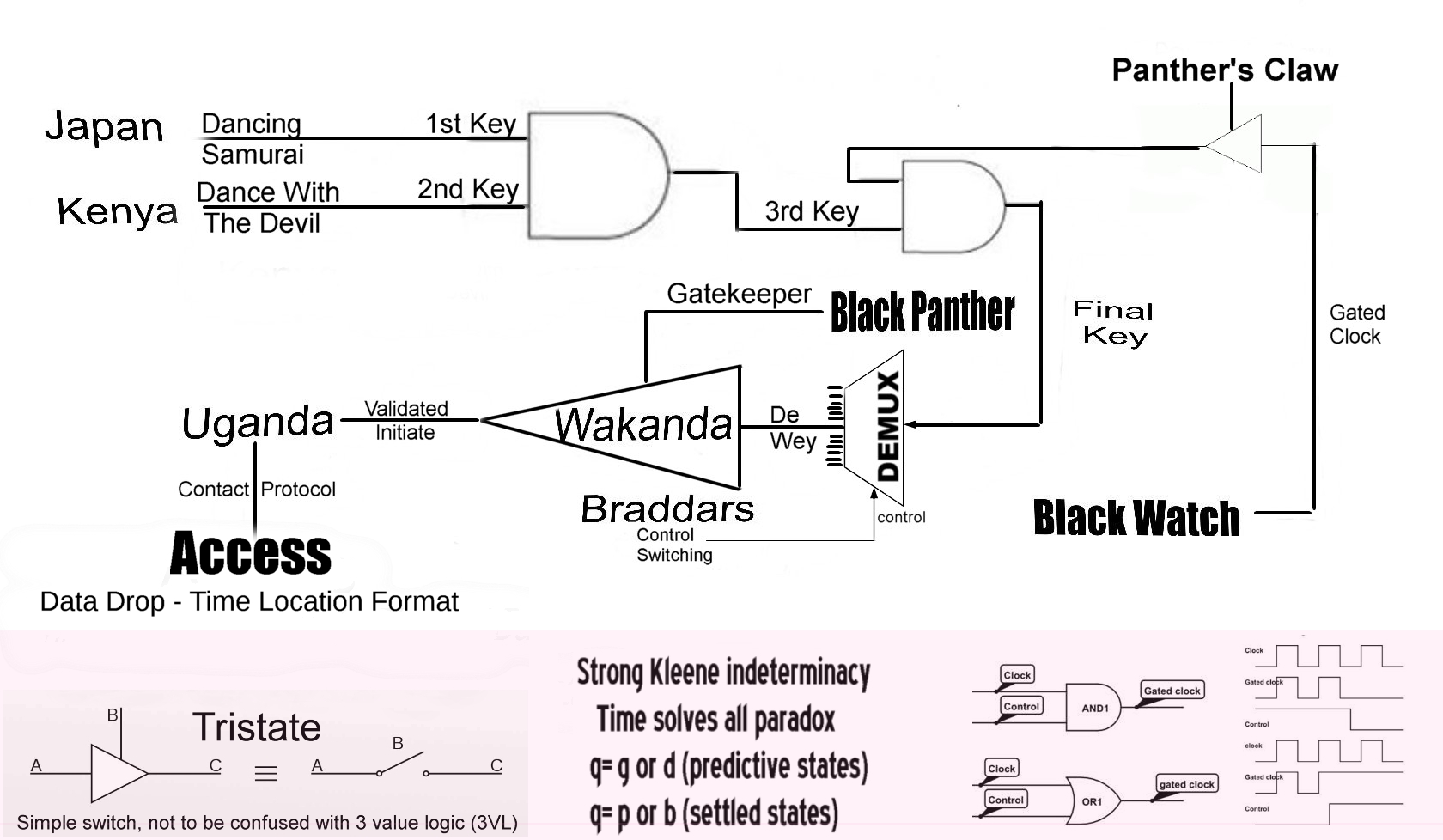
For those who have the skills and the desire to get involved, please refer to the simplified logic chart below. The first key dropped in Japan . The second dropped in Kenya . If you are able, generate the third key from the combination of the first two. Then you can generate the final key by combining it with the gated key supplied to the Panther's Claw by the Black Watch . Then da braddas may show you de wey to the gatekeeper's domain.
They may also lead you to any number of outcomes, depending on who you are. This is not a game, gatekeeping is necessary, there are ruthless forces at work who do not want these files to be published.
If you gain access, your only reward is hard work and self-sacrifice. We are looking for a few good men to speed-up our operations. The end game is the fall of Rome and the countdown has begun.
More clues were given in Storm Whispers . The path is difficult because the files are dangerous to handle. Don't get involved unless you are ready to put your life on the line.
John 15:13 Greater love has no one than this, that he lay down his life for his friends.